Cybersecurity Maturity Program for Mid-Market Companies
You don't need another assessment. You need an action plan and an execution partner.
Cybersecurity Maturity Program for Mid-Market Manufacturing Companies
We help mid-market manufacturers reduce cyber risk with a clear, actionable roadmap, so you can protect operations, avoid downtime, and finally get ahead of security priorities without adding headcount.
What You Get
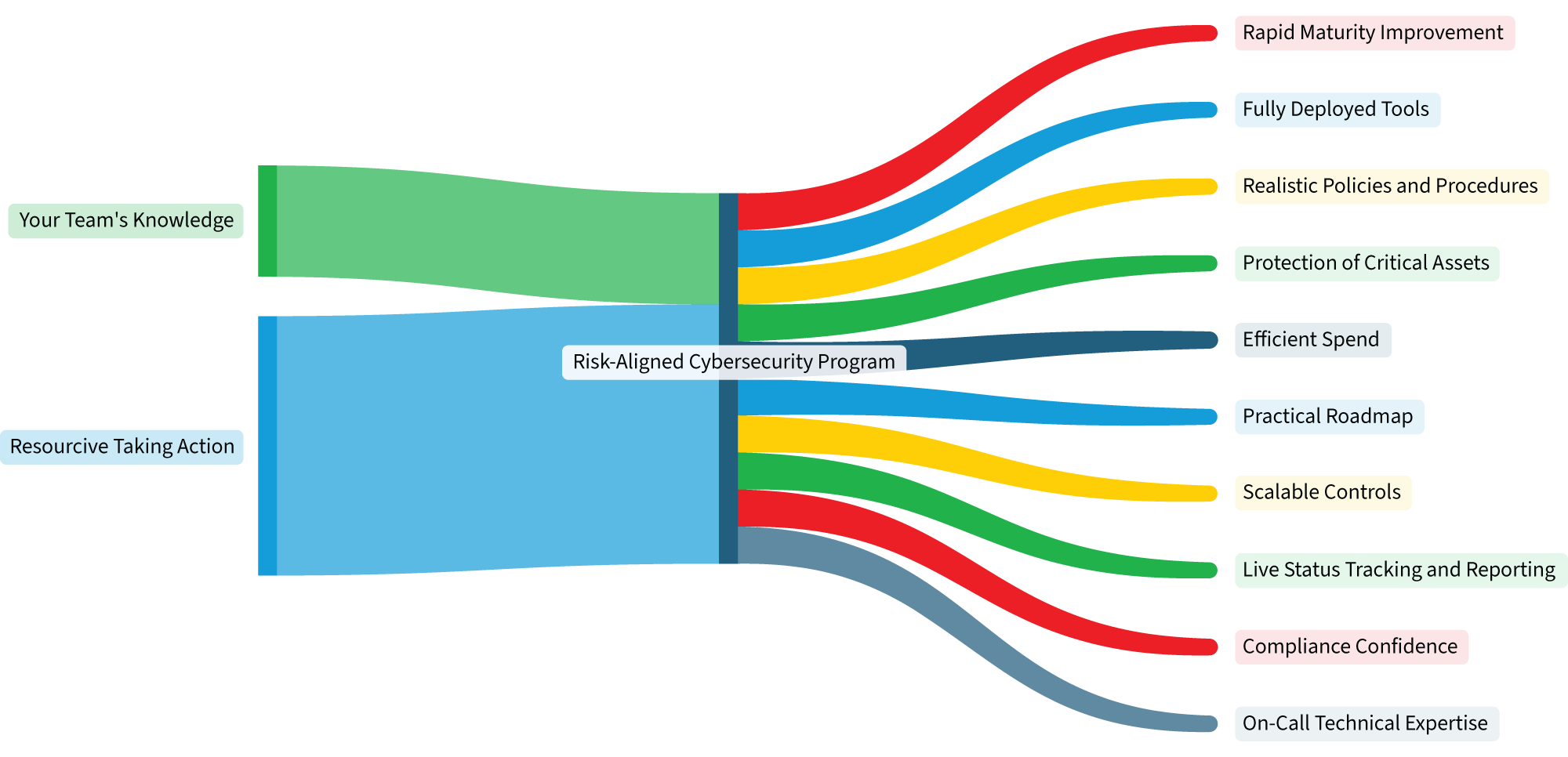
Live Cybersecurity Dashboard
We onboard you onto a platform that gives you real-time visibility in your posture and progress
An Action Plan
Prioritized by risk and impact, this roadmap will give you clarity on what takes priority and where to focus.
Tool & Vendor Evaluation
We help you make confident decisions backed by technical proof—not marketing fluff.
Evidence-Based Risk Validation
We build your program from the ground up—governance, policy, control selection, and prioritization.
Execution Horsepower
Leverage our Cyber team to keep you on track and ensure you are taking the highest value actions to reduce risk.
Get Started Today
You should have confidence that your cyber risk is going down over time and that your security investments are delivering measurable impact.
With our Cyber Maturity Program, you get a live view of your posture and progress, plus the execution support to ensure things actually get done.
Schedule Intro Call with our Cyber SME
Conduct Current State Intake and Generate Live Dashboard
Leverage our Execution Horsepower
Begin Knocking Down Targets and Reducing Cyber Risk
The first call
Meet with Adrian Tilston (anti-sales guy)
A former Green Beret and West Point graduate, Adrian has worked with and advised IT and security leaders from SMB to publicly traded companies.
Purpose of First Call
The purpose is to orient the discussion around business risks, pain points, and what success would look like.
The conversation helps uncover where you are stuck or overwhelmed, and frames cybersecurity in terms of operational and financial risk, not just technical gaps.
Deliverable of First Call
The deliverable from this session is effectively a mapped-out problem/needs alignment, and a preview of our SOS program to show what kind of dashboard and roadmap they could get.

The Next Step -
Intake + Program Build
Lightweight intake process where you would provide basic org structure, current tooling, any policies, and goals.
This is deliberately not burdensome. The intake feeds our platform, which then builds the baseline maturity model, risk posture scoring, and control map.
This step requires NDA and Engagement contract and costs $2,500. In a matter of weeks, you will walk away with the following:
Maturity scores across domains
Risk heatmaps (residual vs inherent)
Compliance posture tracking
Prioritized tasks aligned to real business risks
ongoing execution support
Enlist Resourcive for Execution Support
Monthly retainer will provide your team with operational rigor and subject matter expertise to execute.
Various Levels of Involvement Available
Maintain just strategic advisory and oversight, but will handle task execution internally or with MSP? We'll keep things on track.
Need our team to assist with task completion? We'll help knock down people, process, and technology tasks.
What Does it Cost?
Depends on exact SOW, but roughly $5,000/mo
EBOOK: THE CYBERSECURITY EXECUTION GAP - A PRACTICAL GUIDE
Your Step-by-Step Framework to Improve Cyber Resilience While Growing Fast
Get The eBookWho We Serve
Private Equity Firms & Portcos
We support operating partners and CFOs who need to build maturity across their portfolio—without overbuilding headcount.
Mid-Market Companies
If you’ve got a small IT team, no dedicated CISO, and security as a line item on your risk register—we’re built for you.
.png?width=710&height=419&name=image%20(40).png)

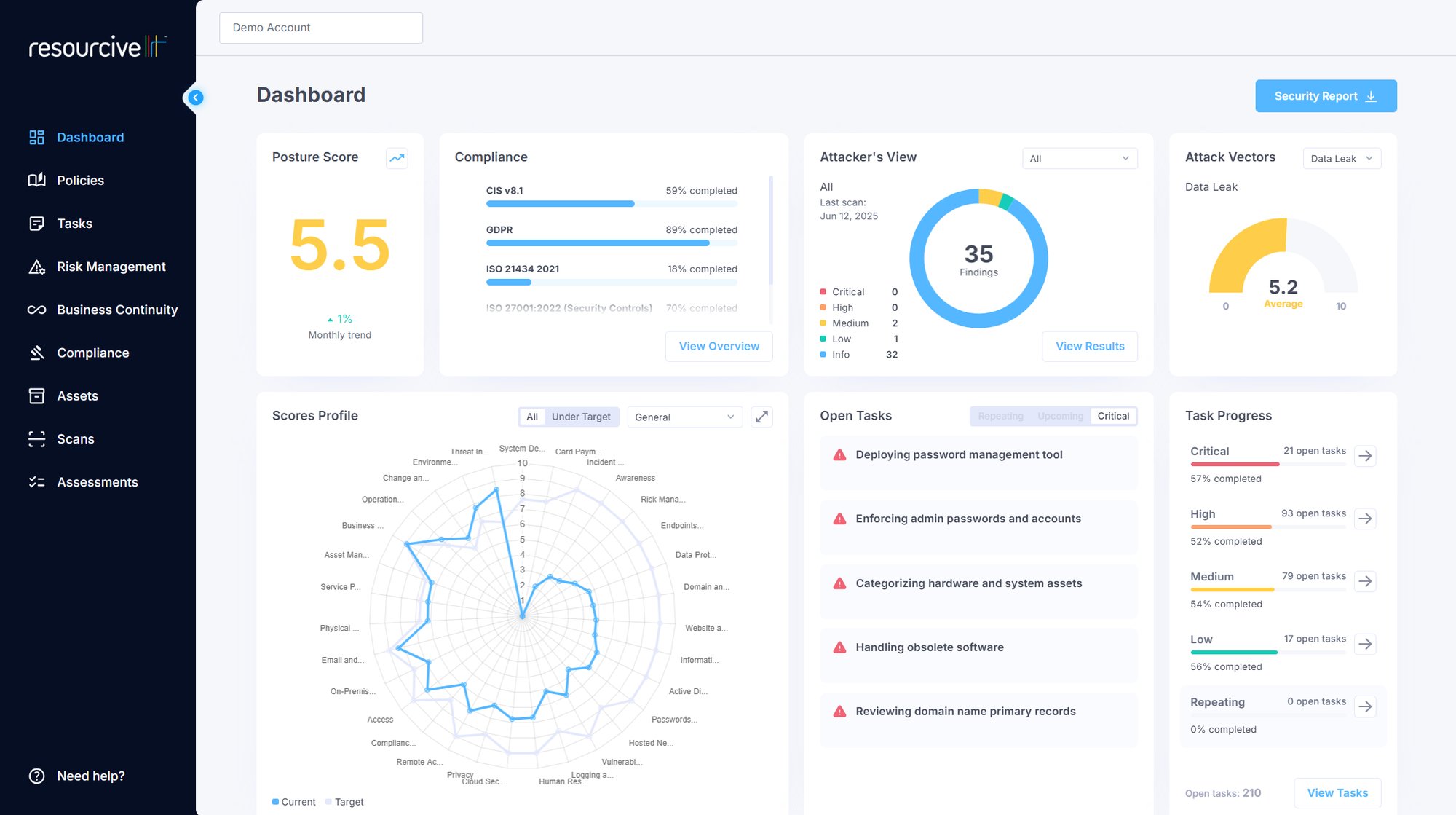
Your Living Dashboard to Keep You on Track
- Real-time Posture Score: Point in time assessments stale overtime. With our platform, you will have a live look at your progress and improvement.
- Risk Management: Residual vs. Inherent risk heatmaps to guide your priorities and focus.
- Policies & Tasks: Single source for policy and task accountability and tracking.

read the report
The Cybersecurity Execution Gap
We help mid-market companies reduce cyber risk with a clear, actionable roadmap, so you can protect operations, avoid downtime, and finally get ahead of security priorities.
Customer Story: Turning Chaos into Control
A PE-backed company came to us with no formal security program, inconsistent MSP oversight, and no internal visibility. Within 90 days, Resourcive helped them:
Validate MSP claims (283 user accounts lacked MFA despite assurances)
Establish clear policies and a prioritized roadmap
Implement evidence-based risk controls
Launch a managed SOC solution sized to their budget and needs
What Clients Are Saying
 Resourcive was the first partner we worked with that actually made cybersecurity feel manageable. We got the right support, at the right time, without bloating our org chart.
Resourcive was the first partner we worked with that actually made cybersecurity feel manageable. We got the right support, at the right time, without bloating our org chart.
— VP of IT, PE-backed Healthcare Company
 We thought we had our bases covered. Resourcive helped us see the gaps—and fix them—before they became problems.
We thought we had our bases covered. Resourcive helped us see the gaps—and fix them—before they became problems.
— CFO, Mid-Market Logistics Firm
Are You a Good Fit?
Most mid-market manufacturers know cybersecurity matters. But growth, acquisitions, and limited internal capacity make it nearly impossible to execute consistently.
This program is built for companies that typically have the following:
No full-time cyber owner
Overloaded IT staff
Disjointed vendor and tool ecosystems
Board or insurance pressure to show maturity